HOW IT WORKS
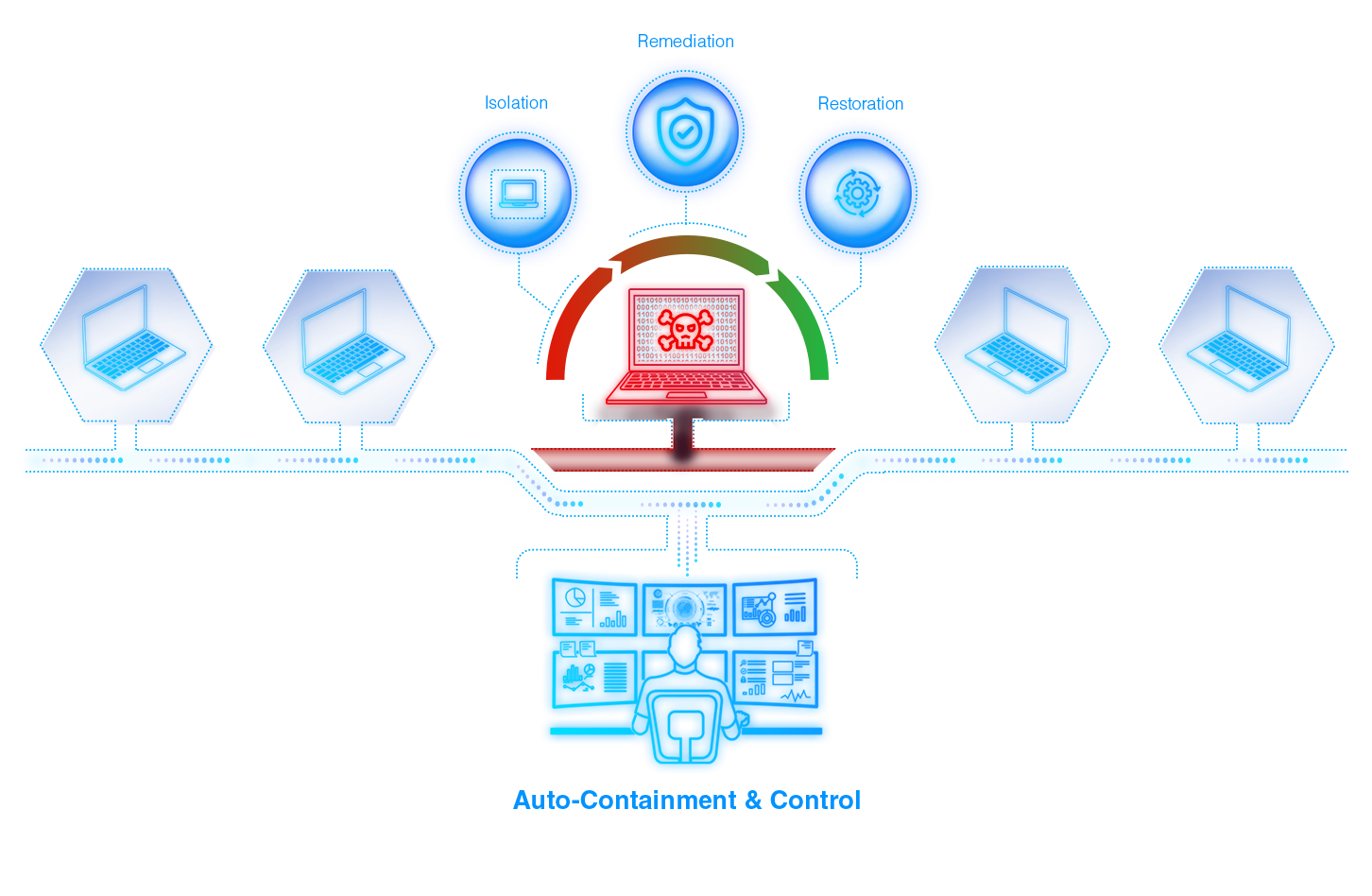

Automated Isolation of Affected Entities Prevents Advancement Of Threat Vector and Controls The Damage
An Intelligent Technique to Stop Lateral Movement of Malware and Threat Carriers
Our AI-powered auto isolation feature disconnects the affected entity from the rest of the network and prevents the further spread of the threat and minimizes the damage.
The affected system is sent to a sandbox environment and is being diagnosed for the problem in a secure environment. The sandbox zone is used to determine the type of vulnerability and possible solution.
Though the affected sytems are isolated from the internal network, the support control system provides privileged access to a security analyst for investigation and recovery.
The checked and remediated entity is restored back to its original network and available for use without any intervention of the local IT team.
Reduced burden on cyber security and IT teams
Automation provides real-time blocker to control damage
Prevention of collateral damage and eduction in business and financial loss
Seamless availability of containment and restoration system without human intervention

Blog

[:en]Do you ever wonder about the pre-built software in your computer? What will happen if it affects your security? What is the worst-case scenario? A pre-installed piece in your computer can pose a serious security risk [...][:fi]Oletko koskaan miettinyt esiasennetun ohjelmiston aiheuttamaa mahdollista tietoturvariskiä tietokoneessasi? Mikä on pahin mahdollinen skenaario? Syytä huoleen on, sillä esiasennettu ohjelma tietokoneessasi voi aiheuttaa vakavan tietoturvariskin [...][:no]Har du noen gang lurt på den forhåndsbygde programvaren på datamaskinen din? Hva vil skje hvis det påvirker sikkerheten din? Hva er det verste scenarioet? En forhåndsinstallert del i datamaskinen din kan utgjøre en alvorlig sikkerhetsrisiko […][:se]Undrar du någonsin över den inbyggda programvaran i datorn? Vad händer om den påverkar säkerheten? Vilket är det värsta tänkbara scenariot? Ett förinstallerad program i datorn kan utgöra en allvarlig säkerhetsrisk [...][:]
Read MoreBlog

[:en]Citrix Systems, Inc. is an American multinational software company that provides server, application & desktop virtualization, networking, software as a service (SaaS), and cloud computing technologies [...][:fi]Citrix Systems, Inc. on yhdysvaltalainen monikansallinen ohjelmistoyritys, joka tarjoaa palvelin-, sovellus- ja työpöytävirtualisointia, verkkoteknologioita, ohjelmistoa palveluna (SaaS) ja pilvipalveluteknologioita [...][:no]Citrix Systems, Inc. er et amerikansk multinasjonalt programvareselskap som leverer server-, applikasjons- og skrivebordsvirtualisering, nettverk, programvare som en tjeneste (SaaS) og cloud computing-teknologier [...][:se]Citrix Systems, Inc. är ett amerikanskt multinationellt programvaruföretag som tillhandahåller servrar, tillämpnings- och datorvirtualiseringar, nätverk, programvara som tjänst (SaaS) och molntekniker [...][:]
Read MoreBlog

[:en]Technology is constantly evolving, and so is its relevance. In today’s world, its increasingly difficult to imagine a day without technology. Just think of the number of times that you rely on new age technologies for each activity [...][:fi]Teknologia kehittyy jatkuvasti, ja samoin sen merkitys. Nykypäivän maailmassa on yhä vaikeampaa kuvitella päivää ilman teknologiaa. Mieti kuinka monta kertaa luotat uuden ajan teknologioihin jokaisessa toiminnassasi [...][:no]Teknologien er i konstant utvikling, og det samme er dens relevans. I dagens verden er det stadig vanskeligere å forestille seg en dag uten teknologi. Bare tenk på hvor mange ganger du stoler på nye tidsalderteknologier for hver aktivitet [...][:se]Tekniken utvecklas hela tiden och det gör dess relevans också. I dagens värld är det allt svårare att tänka sig en dag utan teknik. Tänk bara alla de gånger du förlitar dig på nya tekniker för alla aktiviteter [...][:]
Read More