How it Works
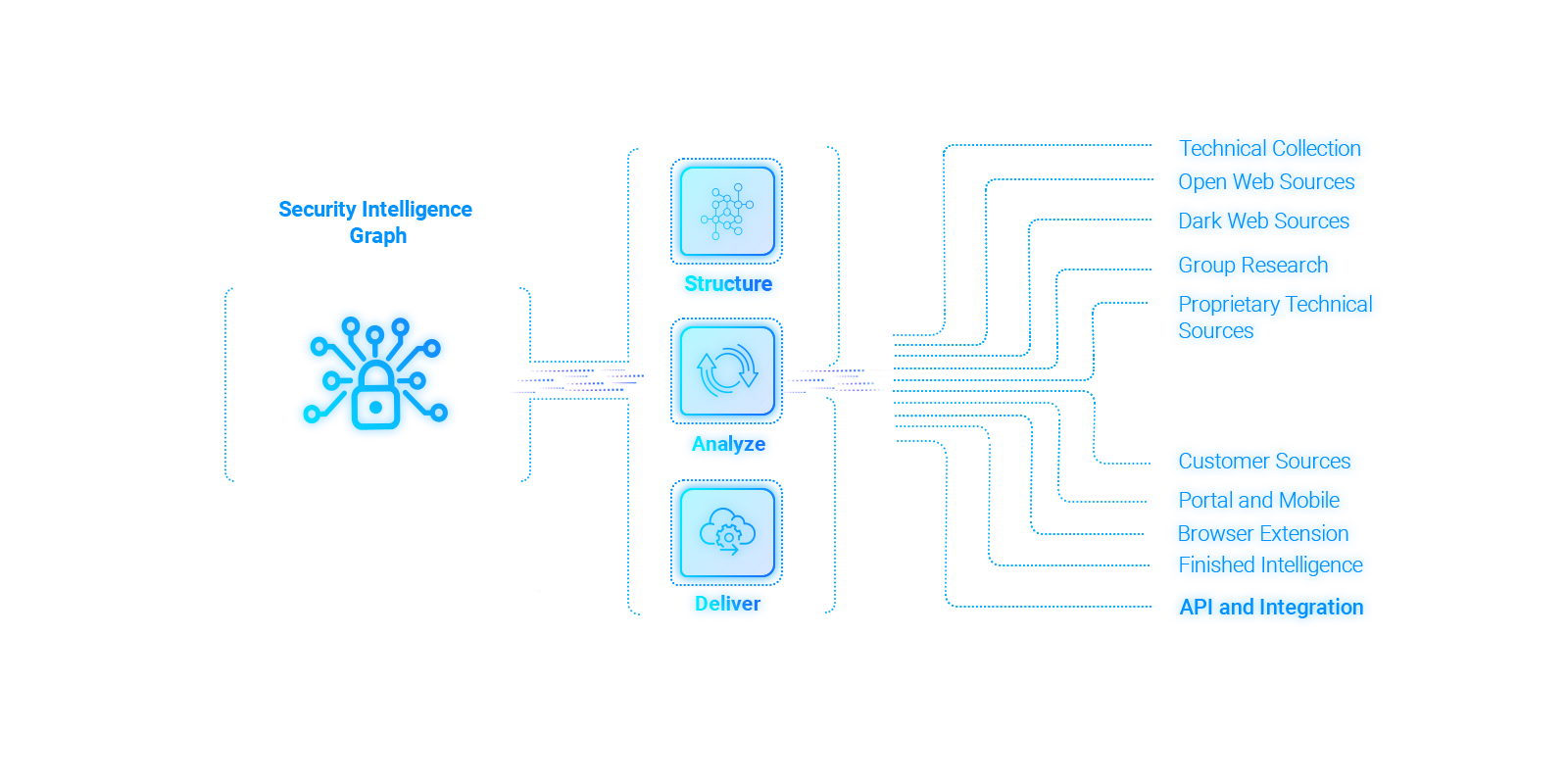

Providing enhanced visibility to monitor activities happening on Surface Web, Dark Web, I2P & other Invisible Platforms.
Holistic Protection Suite to Safeguard your Digital Assets from Modern-Day Threats
Industry specific threat monitoring
VIP Identity Theft detection.
Domain abuse Detection.
Email domain Security
Insignia Protection & risk mitigation
Data leakage monitoring and tracing
Brand impersonation / Fake Identity
Application, URL and file sandboxing
Robust SIEM, SOAR reporting of actionable
Advanced Alert triage in SIEM and SOAR
Proactive Threat detection
Block-grade indicators
Monitoring of Dark web, Closed Forum, deep web and Onion sites
Monitoring coverage of DNS Records, social media, Messaging Platforms, Paste Sites, Mobile App Stores and Open Apps.

Blog

[:en]Citrix Systems, Inc. is an American multinational software company that provides server, application & desktop virtualization, networking, software as a service (SaaS), and cloud computing technologies [...][:fi]Citrix Systems, Inc. on yhdysvaltalainen monikansallinen ohjelmistoyritys, joka tarjoaa palvelin-, sovellus- ja työpöytävirtualisointia, verkkoteknologioita, ohjelmistoa palveluna (SaaS) ja pilvipalveluteknologioita [...][:no]Citrix Systems, Inc. er et amerikansk multinasjonalt programvareselskap som leverer server-, applikasjons- og skrivebordsvirtualisering, nettverk, programvare som en tjeneste (SaaS) og cloud computing-teknologier [...][:se]Citrix Systems, Inc. är ett amerikanskt multinationellt programvaruföretag som tillhandahåller servrar, tillämpnings- och datorvirtualiseringar, nätverk, programvara som tjänst (SaaS) och molntekniker [...][:]
Read MoreBlog

[:en]Do you ever wonder about the pre-built software in your computer? What will happen if it affects your security? What is the worst-case scenario? A pre-installed piece in your computer can pose a serious security risk [...][:fi]Oletko koskaan miettinyt esiasennetun ohjelmiston aiheuttamaa mahdollista tietoturvariskiä tietokoneessasi? Mikä on pahin mahdollinen skenaario? Syytä huoleen on, sillä esiasennettu ohjelma tietokoneessasi voi aiheuttaa vakavan tietoturvariskin [...][:no]Har du noen gang lurt på den forhåndsbygde programvaren på datamaskinen din? Hva vil skje hvis det påvirker sikkerheten din? Hva er det verste scenarioet? En forhåndsinstallert del i datamaskinen din kan utgjøre en alvorlig sikkerhetsrisiko […][:se]Undrar du någonsin över den inbyggda programvaran i datorn? Vad händer om den påverkar säkerheten? Vilket är det värsta tänkbara scenariot? Ett förinstallerad program i datorn kan utgöra en allvarlig säkerhetsrisk [...][:]
Read MoreBlog

[:en]Technology is constantly evolving, and so is its relevance. In today’s world, its increasingly difficult to imagine a day without technology. Just think of the number of times that you rely on new age technologies for each activity [...][:fi]Teknologia kehittyy jatkuvasti, ja samoin sen merkitys. Nykypäivän maailmassa on yhä vaikeampaa kuvitella päivää ilman teknologiaa. Mieti kuinka monta kertaa luotat uuden ajan teknologioihin jokaisessa toiminnassasi [...][:no]Teknologien er i konstant utvikling, og det samme er dens relevans. I dagens verden er det stadig vanskeligere å forestille seg en dag uten teknologi. Bare tenk på hvor mange ganger du stoler på nye tidsalderteknologier for hver aktivitet [...][:se]Tekniken utvecklas hela tiden och det gör dess relevans också. I dagens värld är det allt svårare att tänka sig en dag utan teknik. Tänk bara alla de gånger du förlitar dig på nya tekniker för alla aktiviteter [...][:]
Read More